1. List the companies Google acquired year by year.Briefly describe the strategic implications of each acquisition.
--This is a listing of Google's corporate acquisitions, including acquisitions of both companies and individual products.
- Acquisition Date --Company/Product --Business Area
- September, 2001=>Deja's Usenet archive--Google Groups.
- September, 2001=>Outride, Inc.--Spin-off from Xerox PARC.
- February, 2003=>Pyra Labs--Blogger.
- April, 2003=>Neotonic Software--CRM technology.
- April, 2003=>Applied Semantics--Advertising technology.
- September 30, 2003=>Kaltix--Search engine technology.
- October, 2003=>Sprinks--Paid listings unit of Primedia.
- October, 2003=>Genius Labs--Blogging
- May 10, 2004=>Ignite Logic--Website creation technology.
- June 23, 2004=>Baidu (2.6% stake)--Chinese language search engine.
- July 13, 2004=>Picasa--Photo management software.
- October 27, 2004=>Keyhole, Inc.--Mapping software; used in Google Earth.
- October 2004=>Where2--Mapping software; used in Google Maps.
- Sept.-Dec., 2004=>ZipDash--Used in Google Ride Finder.
- 2005=>2Web Technologies--Web-based spreadsheet.
- 2005=>Phatbits--Widget engine.
- March 28, 2005=>Urchin Software Corporation--Web analysis.
- May 12, 2005=>Dodgeball--Social networking.
- July, 2005=>Reqwireless--Web browser and Mobile email.
- July 7, 2005=>Current Communications Group--Broadband internet.
- August 17, 2005=>Android (mobile phone platform)--Software for Handheld devices. November,
- 2005=>Skia--Graphics software.
- Novembe 17, 2005=>Akwan Information Technologies--Latin American internet operations.
- December,2005=>allPAY GmbH, bruNET GmbH--Mobile Solution Provider, Germany.
- December 20, 2005=>AOL (5% stake)--Internet.
- January 17, 2006=>dMarc Broadcasting--Radio advertising software and platform.
- February 14, 2006=>Measure Map--Blog analysis.
- March 9, 2006=>Upstartle--Writely, online word processing.
- March 14, 2006=>@Last Software--SketchUp, 3-D modeling.
- April 9, 2006=>Orion--Advanced search method.
- August 15, 2006=>Neven Vision--Computer vision
- October 31, 2006=>JotSpot--Website applications
- November, 2006=>YouTube--Video sharing (San Bruno, CA)
- December, 2006=>Endoxon--Mapping solutions
- January, 2007=>Xunlei (partial acquisition)--Network, file-sharing.
- February, 2007=>Adscape--Video game advertising
- March, 2007=>Trendalyzer--Software
- April, 2007=>Tonic Systems--Presentation software
- April, 2007=>Marratech video conferencing software--Video conferencing (Stockholm, Sweden)
- April 13, 2007=>DoubleClickOnline Advertising
- May 11, 2007=>GreenBorder Technologies--Desktop enterprise security
- June 1, 2007=>Panoramio--Geospatial Photo-sharing Service
- June 3, 2007=>FeedBurner--RSS Feeds (Chicago, IL)
- June 5, 2007=>PeakStream--Parallel Processing
- June, 2007=>Zenter--Presentations Software
- July 2, 2007=>GrandCentral--VOIP Phone Aggregation (Fremont, CA)
- July, 2007=>ImageAmerica--High resolution aerial cameras July 9, 2007=>Postini--Communications Security (San Carlos, CA)
- September, 2007=>Tusli--Google Blogger Api Engineering Team
- September, 2007=>Zingku--Mobile social network and communication platform
- October, 2007=>Jaiku--An activity stream and presence sharing service that works from the Web and mobile phones (Helsinki)
reference to : List of Google acquisitions by Wikip web site
--strategic of the companies Google acquired :
- expanding the web2.0 correlative development
- merge the company of competitor
2. Summarize the What is Web 2.0 by Tim O'Reilly in one page.
Design Patterns and Business Models for the Next Generation of Software by Tim O'Reilly 09/30/2005
The concept of "Web 2.0" began with a conference brainstorming session between O'Reilly and MediaLive International.
1. The Web As Platform
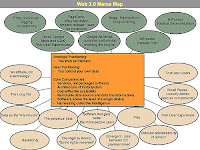
--Figure 1 shows a "meme map" of Web 2.0 that was developed at a brainstorming session during FOO Camp, a conference at O'Reilly Media. It's very much a work in progress, but shows the many ideas that radiate out from the Web 2.0 core.
--At the first Web 2.0 conference, in October 2004, John Battelle and I listed a preliminary set of principles in our opening talk. The first of those principles was "The web as platform." Yet that was also a rallying cry of Web 1.0 darling Netscape, which went down in flames after a heated battle with Microsoft. What's more, two of our initial Web 1.0 exemplars, DoubleClick and Akamai, were both pioneers in treating the web as a platform.
2. Harnessing Collective Intelligence
--Network effects from user contributions are the key to market dominance in the Web 2.0 era.
l Blogging and the Wisdom of Crowds.
--One of the most highly touted features of the Web 2.0 era is the rise of blogging.
--A blog is just a personal home page in diary format. But as Rich Skrenta
notes, the chronological organization of a blog "seems like a trivial difference, but it drives an entirely different delivery, advertising and value chain."
3. Data is the Next Intel Inside
--Every significant internet application to date has been backed by a specialized database: Google's web crawl, Yahoo!'s directory (and web crawl), Amazon's database of products, eBay's database of products and sellers, MapQuest's map databases, Napster's distributed song database. As Hal Varian remarked in a personal conversation last year, "SQL is the new HTML." Database management is a core competency of Web 2.0 companies, so much so that we have sometimes referred to these applications as "
infoware" rather than merely software.
4. End of the Software Release Cycle
--One of the defining characteristics of internet era software is that it is delivered as a service, not as a product. This fact leads to a number of fundamental changes in the business model of such a company: Operations must become a core competency.
--Users must be treated as co-developers, in a reflection of open source development practices.
5. Lightweight Programming Models
--Support lightweight programming models that allow for loosely coupled systems.
--Think syndication, not coordination.
--Design for "hackability" and remixability.
--Another key web 2.0 principle, which we call "innovation in assembly.", we believe that Web 2.0 will provide opportunities for companies to beat the competition by getting better at harnessing and integrating services provided by others.
6. Software Above the Level of a Single Device
--One other feature of Web 2.0 that deserves mention is the fact that it's no longer limited to the PC platform. In his parting advice to Microsoft, long time Microsoft developer Dave Stutz pointed out that "Useful software written above the level of the single device will command high margins for a long time to come."
--But as with many areas of Web 2.0, where the "2.0-ness" is not something new, but rather a fuller realization of the true potential of the web platform, this phrase gives us a key insight into how to design applications and services for the new platform.
7. Rich User Experiences
--The competitive opportunity for new entrants is to fully embrace the potential of Web 2.0. Companies that succeed will create applications that learn from their users, using an architecture of participation to build a commanding advantage not just in the software interface, but in the richness of the shared data.
Summarizing the Core Competencies of Web 2.0 Companies:
.--Services, not packaged software, with cost-effective scalability
.--Control over unique, hard-to-recreate data sources that get richer as more people use them
.--Trusting users as co-developers
.--Harnessing collective intelligence
.--Leveraging the long tail through customer self-service
.--Software above the level of a single device
.--Lightweight user interfaces, development models, AND business models